-
Latest Version
Google Chrome 124.0.6367.119 LATEST
-
Review by
-
Operating System
macOS 10.15 Catalina or later
-
User Rating
Click to vote -
Author / Product
-
Filename
googlechrome.dmg
In addition to the browser app itself, Google also released the source code of this app under an open-source Chromium license, enabling other developers to create variations of this browser and implement other unique features into its basic feature set.
Today, 15 years after it was released to the public, this browser represents a staggering 67% of the worldwide browser market share. The browser's fast performance and built-in security features make it a popular choice for users on Apple's desktop operating system.
Main Features
- Easy-to-use interface – Browse the web using a clean and minimalist interface.
- Compatibility with various Google services – Access seamless integration with services such as Gmail, Google Drive, and Google Calendar.
- Reliable Web Rendering – Correctly renders advanced webapps and services powered by modern cloud platforms.
- Extensive Customization Options – Enhance the browsing experience through numerous extensions and add-ons.
- Chrome Web Store – The home of the incredible catalog of Chrome extensions, add-ons, and web apps.
- Advanced Desktop Shortcuts – Transform webapps into streamlined app windows that are started via regular desktop shortcuts.
- Advanced Privacy – Browse the web safely and anonymously using built-in Incognito mode.
- Fast performance – Experience all web content in a fast and responsive manner.
- Built-in security features – Browse safely with automatic security features that prevent visiting dangerous websites.
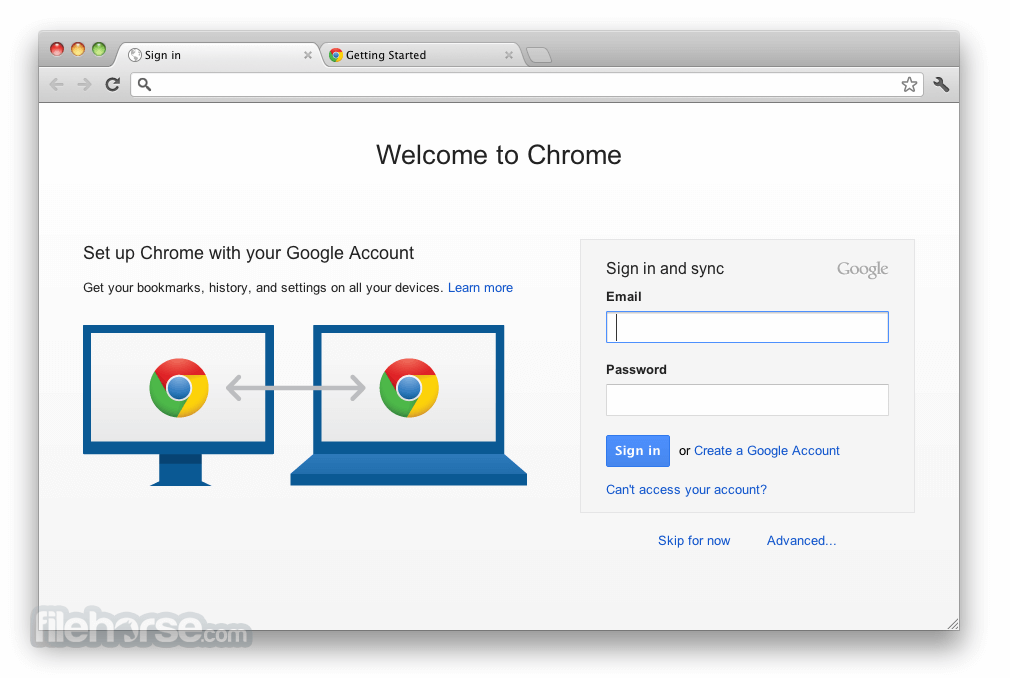
To install this popular browser on any modern Mac computer, users simply need to download the official installer from the secure FileHorse servers or the app’s official website. The installation procedure is fully automated and requires users only to follow a few simple on-screen instructions, including a check for a primary browser and optional creation of a Google account.
The browser is compatible with macOS Catalina 10.15 or later.
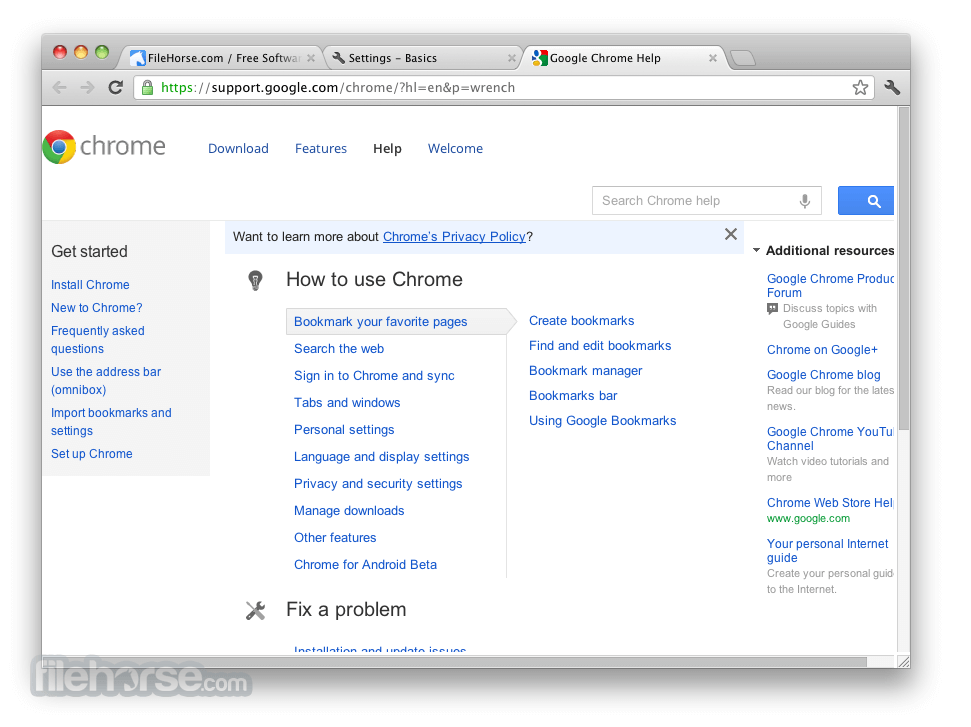
How to Use
To use Google Chrome on a Mac, users can simply open this browser app and enter the desired URL in the address bar to navigate to a specific website. The browser allows for easy creation and management of bookmarks, and it also has many convenient services such as a simple download manager, task viewer of browser-related processes, tab management tools, and more.
Users are also empowered to easily access various Google services and tools through the browser, such as Gmail, Google Drive, Google Calendar, and Google Translate. Additionally, users can dramatically increase the capabilities of this browser by installing extensions and add-ons, which can add streamlined access to external services such as password managers, email checkers, ad blockers, and more.
User Interface
The app has a clean and minimalist interface, making it visually appealing and easy to navigate. While there are not many customization options available, users can optimize the use of this browser by creating their own bookmarks and arranging links in the shortcut bar located just before the URL address field.
FAQ
What is Google Chrome for macOS?
It is a modern web browser developed by Google that offers a range of features and functionalities. It is regarded as the most popular and capable browser currently available on the market.
Is it safe?
Yes. This app comes bundled with built-in security features to prevent visiting dangerous websites and detecting malware and is regularly updated by developers at Google.
Alternatives
Safari – Apple's native browser, known for its optimized performance on Apple devices and its cloud services.
Firefox – A popular non-Chromium alternative browser app with a large selection of add-ons and excellent developer tools.
Brave – A privacy-focused browser that blocks ads and trackers by default.
Opera for Mac – A versatile web browser, offering users a fast, secure, and feature-rich browsing experience on the macOS.
Microsoft Edge – A fast, secure, and modern web browsing experience, seamlessly integrating with the macOS platform for enhanced productivity and convenience.
Pricing
This app is 100% free for use.
System Requirements
Developers from Google have optimized this app for macOS Catalina 10.15 or later.
PROS
- Excellent compatibility with modern web destinations.
- Easy-to-use interface.
- Compatibility with various Google services.
- Fast performance.
- Built-in security features.
- Data mining concerns.
- Resource intensive.
- Does not offer extensive customization options.
Google Chrome for Mac is a versatile and feature-rich web browser that offers a wide range of functionalities and customization options to users of all ages and knowledge levels. It is best known for its easy-to-use interface, compatibility with various Google services, fast performance, and a base on which many other alternative Chromium browsers are made.
Also Available: Download Google Chrome for Windows
What's new in this version:
Google Chrome 124.0.6367.119
Security Fixes:
- High CVE-2024-4331: Use after free in Picture In Picture
- High CVE-2024-4368: Use after free in Dawn
Google Chrome 124.0.6367.80
Security fixes:
- Critical CVE-2024-4058: Type Confusion in ANGLE
- High CVE-2024-4059: Out of bounds read in V8 API
- High CVE-2024-4060: Use after free in Dawn
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 124.0.6367.62
- Change log not available for this version
Google Chrome 123.0.6312.124
Security Fixes and Rewards:
- High CVE-2024-3157: Out of bounds write in Compositing
- High CVE-2024-3516: Heap buffer overflow in ANGLE
- High CVE-2024-3515: Use after free in Dawn
Google Chrome 123.0.6312.87
Security fixes:
- Critical CVE-2024-2883: Use after free in ANGLE
- High CVE-2024-2885: Use after free in Dawn
- High CVE-2024-2886: Use after free in WebCodecs
- High CVE-2024-2887: Type Confusion in WebAssembly
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 123.0.6312.59
Security Fixes:
- High CVE-2024-2625: Object lifecycle issue in V8
- Medium CVE-2024-2626: Out of bounds read in Swiftshader
- Medium CVE-2024-2627: Use after free in Canvas
- Medium CVE-2024-2628: Inappropriate implementation in Downloads
- Medium CVE-2024-2629: Incorrect security UI in iOS
- Medium CVE-2024-2630: Inappropriate implementation in iOS
- Low CVE-2024-2631: Inappropriate implementation in iOS
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 122.0.6261.129
Security fixes:
- High CVE-2024-2400: Use after free in Performance Manager
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 122.0.6261.112
Security Fixes:
- High CVE-2024-2173: Out of bounds memory access in V8
- High CVE-2024-2174: Inappropriate implementation in V8
- High CVE-2024-2176: Use after free in FedCM
Google Chrome 122.0.6261.94
Security Fixes :
- High: Type Confusion in V8
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 122.0.6261.69
- Change log not available for this version
Google Chrome 122.0.6261.57
Security fixes:
- High CVE-2024-1669: Out of bounds memory access in Blink
- High CVE-2024-1670: Use after free in Mojo
- Medium CVE-2024-1671: Inappropriate implementation in Site Isolation
- Medium CVE-2024-1672: Inappropriate implementation in Content Security Policy
- Medium CVE-2024-1673: Use after free in Accessibility
- Medium CVE-2024-1674: Inappropriate implementation in Navigation
- Medium CVE-2024-1675: Insufficient policy enforcement in Download
- Low CVE-2024-1676: Inappropriate implementation in Navigation
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 121.0.6167.184
- Change log not available for this version
Google Chrome 121.0.6167.160
Security Fixes:
- High CVE-2024-1284: Use after free in Mojo
- High CVE-2024-1283: Heap buffer overflow in Skia
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 121.0.6167.139
Security Fixes:
- Use after free in Canvas
- Use after free in WebRTC
- Use after free in Network
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 121.0.6167.85
Security Fixes:
- High CVE-2024-0807: Use after free in WebAudio
- High CVE-2024-0812: Inappropriate implementation in Accessibility
- High CVE-2024-0808: Integer underflow in WebUI
- Medium CVE-2024-0810: Insufficient policy enforcement in DevTools
- Medium CVE-2024-0814: Incorrect security UI in Payments
- Medium CVE-2024-0813: Use after free in Reading Mode
- Medium CVE-2024-0806: Use after free in Passwords
- Medium CVE-2024-0805: Inappropriate implementation in Downloads
- Medium CVE-2024-0804: Insufficient policy enforcement in iOS Security UI
- Low CVE-2024-0811: Inappropriate implementation in Extensions API
- Low CVE-2024-0809: Inappropriate implementation in Autofill
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 120.0.6099.199
- Change log not available for this version
Google Chrome 120.0.6099.129
- Change log not available for this version
Google Chrome 120.0.6099.109
Security Fixes:
- High CVE-2023-6702: Type Confusion in V8
- High CVE-2023-6703: Use after free in Blink
- High CVE-2023-6704: Use after free in libavif
- High CVE-2023-6705: Use after free in WebRTC
- High CVE-2023-6706: Use after free in FedCM
- Medium CVE-2023-6707: Use after free in CSS
- [1510677] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 120.0.6099.62
Security Fixes and Rewards:
- High CVE-2023-6508: Use after free in Media Stream
- High CVE-2023-6509: Use after free in Side Panel Search
- Medium CVE-2023-6510: Use after free in Media Capture
- Low CVE-2023-6511: Inappropriate implementation in Autofill
- Low CVE-2023-6512: Inappropriate implementation in Web Browser UI
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 119.0.6045.199
Security fixes:
- High CVE-2023-6348: Type Confusion in Spellcheck
- High CVE-2023-6347: Use after free in Mojo
- High CVE-2023-6346: Use after free in WebAudio
- High CVE-2023-6350: Out of bounds memory access in libavif
- High CVE-2023-6351: Use after free in libavif
- High CVE-2023-6345: Integer overflow in Skia
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 119.0.6045.159
Security fixes:
- High CVE-2023-5997: Use after free in Garbage Collection
- High CVE-2023-6112: Use after free in Navigation
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 119.0.6045.123
Security fix:
- High CVE-2023-5996: Use after free in WebAudio
Google Chrome 119.0.6045.105
Security fixes:
- High CVE-2023-5480: Inappropriate implementation in Payments
- High CVE-2023-5482: Insufficient data validation in USB
- High CVE-2023-5849: Integer overflow in USB
- Medium CVE-2023-5850: Incorrect security UI in Downloads
- Medium CVE-2023-5851: Inappropriate implementation in Downloads
- Medium CVE-2023-5852: Use after free in Printing
- Medium CVE-2023-5853: Incorrect security UI in Downloads
- Medium CVE-2023-5854: Use after free in Profiles
- Medium CVE-2023-5855: Use after free in Reading Mode
- Medium CVE-2023-5856: Use after free in Side Panel
- Medium CVE-2023-5857: Inappropriate implementation in Downloads
- Low CVE-2023-5858: Inappropriate implementation in WebApp Provider
- Low CVE-2023-5859: Incorrect security UI in Picture In Picture
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 118.0.5993.117
- High CVE-2023-5472: Use after free in Profiles
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 118.0.5993.96
- Change log not available for this version
Google Chrome 118.0.5993.88
- Change log not available for this version
Google Chrome 118.0.5993.70
Security fixes:
- Critical CVE-2023-5218: Use after free in Site Isolation
- Medium CVE-2023-5487: Inappropriate implementation in Fullscreen
- Medium CVE-2023-5484: Inappropriate implementation in Navigation
- Medium CVE-2023-5475: Inappropriate implementation in DevTools
- Medium CVE-2023-5483: Inappropriate implementation in Intents
- Medium CVE-2023-5481: Inappropriate implementation in Downloads
- Medium CVE-2023-5476: Use after free in Blink History
- Medium CVE-2023-5474: Heap buffer overflow in PDF
- Medium CVE-2023-5479: Inappropriate implementation in Extensions API
- Low CVE-2023-5485: Inappropriate implementation in Autofill
- Low CVE-2023-5478: Inappropriate implementation in Autofill
- Low CVE-2023-5477: Inappropriate implementation in Installer
- Low CVE-2023-5486: Inappropriate implementation in Input
- Low CVE-2023-5473: Use after free in Cast
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1491268] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 117.0.5938.149
Security fix:
- High CVE-2023-5346: Type Confusion in V8
Google Chrome 117.0.5938.132
Security fixes:
- High CVE-2023-5217: Heap buffer overflow in vp8 encoding in libvpx
- High CVE-2023-5186: Use after free in Passwords
- High CVE-2023-5187: Use after free in Extensions
Google Chrome 117.0.5938.92
- Change log not available for this version
Google Chrome 117.0.5938.88
- Change log not available for this version
Google Chrome 117.0.5938.62
Security Fixes:
- Critical CVE-2023-4863: Heap buffer overflow in WebP
- Medium CVE-2023-4900: Inappropriate implementation in Custom Tabs
- Medium CVE-2023-4901: Inappropriate implementation in Prompts
- Medium CVE-2023-4902: Inappropriate implementation in Input
- Medium CVE-2023-4903: Inappropriate implementation in Custom Mobile Tabs
- Medium CVE-2023-4904: Insufficient policy enforcement in Downloads
- Medium CVE-2023-4905: Inappropriate implementation in Prompts
- Low CVE-2023-4906: Insufficient policy enforcement in Autofill
- Low CVE-2023-4907: Inappropriate implementation in Intents
- Low CVE-2023-4908: Inappropriate implementation in Picture in Picture
- Low CVE-2023-4909: Inappropriate implementation in Interstitials
Google Chrome 116.0.5845.187
Security Fixes and Rewards:
- Critical CVE-2023-4863: Heap buffer overflow in WebP
Google Chrome 116.0.5845.179
Security Fixes and Rewards:
- High CVE-2023-4761: Out of bounds memory access in FedCM
- High CVE-2023-4762: Type Confusion in V8
- High CVE-2023-4763: Use after free in Networks
- High CVE-2023-4764: Incorrect security UI in BFCache
Google Chrome 116.0.5845.140
Security fixes:
- High CVE-2023-4572: Use after free in MediaStream
Google Chrome 116.0.5845.110
Security Fixes and Rewards:
- High CVE-2023-4430: Use after free in Vulkan
- High CVE-2023-4429: Use after free in Loader
- High CVE-2023-4428: Out of bounds memory access in CSS
- High CVE-2023-4427: Out of bounds memory access in V8
- Medium CVE-2023-4431: Out of bounds memory access in Fonts
Google Chrome 116.0.5845.96
Security Fixes and Rewards:
- High CVE-2023-2312: Use after free in Offline
- High CVE-2023-4349: Use after free in Device Trust Connectors
- High CVE-2023-4350: Inappropriate implementation in Fullscreen
- High CVE-2023-4351: Use after free in Network
- High CVE-2023-4352: Type Confusion in V8
- High CVE-2023-4353: Heap buffer overflow in ANGLE
- High CVE-2023-4354: Heap buffer overflow in Skia
- High CVE-2023-4355: Out of bounds memory access in V8
- Medium CVE-2023-4356: Use after free in Audio
- Medium CVE-2023-4357: Insufficient validation of untrusted input in XML
- Medium CVE-2023-4358: Use after free in DNS
- Medium CVE-2023-4359: Inappropriate implementation in App Launcher
- Medium CVE-2023-4360: Inappropriate implementation in Color
- Medium CVE-2023-4361: Inappropriate implementation in Autofill
- Medium CVE-2023-4362: Heap buffer overflow in Mojom IDL
- Medium CVE-2023-4363: Inappropriate implementation in WebShare
- Medium CVE-2023-4364: Inappropriate implementation in Permission Prompts
- Medium CVE-2023-4365: Inappropriate implementation in Fullscreen
- Medium CVE-2023-4366: Use after free in Extensions
- Medium CVE-2023-4367: Insufficient policy enforcement in Extensions API
- Medium CVE-2023-4368: Insufficient policy enforcement in Extensions API
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 115.0.5790.170
Security Fixes and Rewards:
- High CVE-2023-4068: Type Confusion in V8
- High CVE-2023-4069: Type Confusion in V8
- High CVE-2023-4070: Type Confusion in V8
- High CVE-2023-4071: Heap buffer overflow in Visuals
- High CVE-2023-4072: Out of bounds read and write in WebGL
- High CVE-2023-4073: Out of bounds memory access in ANGLE
- High CVE-2023-4074: Use after free in Blink Task Scheduling
- High CVE-2023-4075: Use after free in Cast
- High CVE-2023-4076: Use after free in WebRTC
- Medium CVE-2023-4077: Insufficient data validation in Extensions
- Medium CVE-2023-4078: Inappropriate implementation in Extensions
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 115.0.5790.114
- Change log not available for this version
Google Chrome 115.0.5790.102
- Change log not available for this version
Google Chrome 114.0.5735.198
Security Fixes and Rewards:
- High CVE-2023-3420: Type Confusion in V8
- High CVE-2023-3421: Use after free in Media
- High CVE-2023-3422: Use after free in Guest View
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1458017] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 114.0.5735.133
- Change log not available for this version
Google Chrome 114.0.5735.106
Security Fixes:
- High CVE-2023-3079: Type Confusion in V8
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 114.0.5735.90
Security Fixes:
- High CVE-2023-2929: Out of bounds write in Swiftshader
- High CVE-2023-2930: Use after free in Extensions
- High CVE-2023-2931: Use after free in PDF
- High CVE-2023-2932: Use after free in PDF
- High CVE-2023-2933: Use after free in PDF
- High CVE-2023-2934: Out of bounds memory access in Mojo
- High CVE-2023-2935: Type Confusion in V8
- High CVE-2023-2936: Type Confusion in V8
- Medium CVE-2023-2937: Inappropriate implementation in Picture In Picture
- Medium CVE-2023-2938: Inappropriate implementation in Picture In Picture
- Medium CVE-2023-2939: Insufficient data validation in Installer
- Medium CVE-2023-2940: Inappropriate implementation in Downloads
- Low CVE-2023-2941: Inappropriate implementation in Extensions API
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 113.0.5672.126
Security Fixes and Rewards:
- Critical CVE-2023-2721: Use after free in Navigation
- High CVE-2023-2722: Use after free in Autofill UI
- High CVE-2023-2723: Use after free in DevTools
- High CVE-2023-2724: Type Confusion in V8
- High CVE-2023-2725: Use after free in Guest View
- Medium CVE-2023-2726: Inappropriate implementation in WebApp Installs
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 113.0.5672.92
- Change log not available for this version
Google Chrome 113.0.5672.63
Security Fixes:
- Medium CVE-2023-2459: Inappropriate implementation in Prompts
- Medium CVE-2023-2460: Insufficient validation of untrusted input in Extensions
- Medium CVE-2023-2461: Use after free in OS Inputs
- Medium CVE-2023-2462: Inappropriate implementation in Prompts
- Medium CVE-2023-2463: Inappropriate implementation in Full Screen Mode
- Medium CVE-2023-2464: Inappropriate implementation in PictureInPicture
- Medium CVE-2023-2465: Inappropriate implementation in CORS
- Low CVE-2023-2466: Inappropriate implementation in Prompts
- Low CVE-2023-2467: Inappropriate implementation in Prompts
- Low CVE-2023-2468: Inappropriate implementation in PictureInPicture
Various fixes from internal audits, fuzzing and other initiatives:
- [M113][DownloadBubble] Compute info relevant to button state in update service
- update_client: remove aggressive CHECK_LE
- [M113 Merge]Fix UAF in ExclusiveAccessBubbleViews
- Remove invalid NOTREACHED() in X11 event parsing
- Fix: Set primary account after sign in interception profile creation
- Updating XTBs based on .GRDs from branch 5672
- [M113][DownloadBubble] Defer GetDownloadManager() calls
- Revert "HttpCache: fix troubles trying to do ranges with empty bodies"
- [M113]Fix PasswordManager.IsPasswordProtected histogram bug
- [MTE] Stop using kReadWriteTagged unless reporting is enabled.
- Removes maxFragmentCombinedOutputResources
- [Start] Build histograms for click rates of Menu button on Start and NTP
- Kill switch flip for BlockFrameRenavigations
- [M113 Merge]Fix: none value enforcing profile separation
- [privacy sandbox] Update widget position on size change
- [Start] Build histogram for click rates of Logo on NTP
- [m113][omnibox][post-ac] Fix switch-to-tab on android with debouncing
- [M113] Fix ScopedObservation UaF in BubbleDialogDelegate::AnchorWidgetObserver
- Updating XTBs based on .GRDs from branch 5672
- Record navigation and unload handler information on every navigation
- [M113]Prerender: Make PrerendererImpl no longer observe PrerenderHost
- [Start] Build histogram for click rates of Home button on NTP
Google Chrome 112.0.5615.137
Security Fixes and Rewards:
- High CVE-2023-2133: Out of bounds memory access in Service Worker API
- High CVE-2023-2134: Out of bounds memory access in Service Worker API
- High CVE-2023-2135: Use after free in DevTools
- High CVE-2023-2136: Integer overflow in Skia
- Medium CVE-2023-2137: Heap buffer overflow in sqlite
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1434139] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 112.0.5615.121
Security Fixes:
- High CVE-2023-2033: Type Confusion in V8
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 112.0.5615.49
- High CVE-2023-1810: Heap buffer overflow in Visuals
- High CVE-2023-1811: Use after free in Frames
- Medium CVE-2023-1812: Out of bounds memory access in DOM Bindings
- Medium CVE-2023-1813: Inappropriate implementation in Extensions
- Medium CVE-2023-1814: Insufficient validation of untrusted input in Safe Browsing
- Medium CVE-2023-1815: Use after free in Networking APIs
- Medium CVE-2023-1816: Incorrect security UI in Picture In Picture
- Medium CVE-2023-1817: Insufficient policy enforcement in Intents
- NA1223346 Medium CVE-2023-1818: Use after free in Vulkan
- NA1406588 Medium CVE-2023-1819: Out of bounds read in Accessibility
- TBD1408120 Medium CVE-2023-1820: Heap buffer overflow in Browser History
- Low CVE-2023-1821: Inappropriate implementation in WebShare
- Low CVE-2023-1822: Incorrect security UI in Navigation
- TBD1406900 Low CVE-2023-1823: Inappropriate implementation in FedCM
Various fixes from internal audits, fuzzing and other initiatives:
- Content Security Policy: Apply strict-dynamic for ScriptSpeculationRules
- aw: Fix metrics service unbinding when not bound
- Updating XTBs based on .GRDs from branch 5615
- CCA: Hide grid lines when grid disabled or not streaming
- Consume history user activation unconditionally when a traversal navigate event has its default prevented
- Only render ntp-lens-upload-dialog in dom once its opened rather than
- [Merge to M112] Prerender: Grant mojo bindings on cross-origin iframes after activation
- Don't crash if a misconfigured printer is missing a URI attribute
- [Merge 112] Site Data Dialog: Stop caching PSCS BDM pointers
- Don't pre-match ::-webkit-scrollbar with trailing selectors
- [M112 merge]: Initialize WaylandTextInputDelegate::pending_focus_reason_ by default
- [M112][RDSG] Use CurrentLog as annotation mode for Synthetic Trial
Google Chrome 111.0.5563.146
- Change log not available for this version
Google Chrome 111.0.5563.110
Security Fixes:
- High CVE-2023-1528: Use after free in Passwords
- High CVE-2023-1529: Out of bounds memory access in WebHID
- High CVE-2023-1530: Use after free in PDF
- High CVE-2023-1531: Use after free in ANGLE
- High CVE-2023-1532: Out of bounds read in GPU Video
- High CVE-2023-1533: Use after free in WebProtect
- High CVE-2023-1534: Out of bounds read in ANGLE
Various fixes from internal audits, fuzzing and other initiatives:
- Revert "Cache hypothetical scrollbar thickness"
- [M111] preload: Record the metrics of triggered mousedown and mouseover
- MediaRecorder: fix duplicate onstart events
- Updating XTBs based on .GRDs from branch 5563
- [Merge to M111] Use Count histograms to account for longer pervasive payloads list
- [M111][infra] Use the actual project in src-side builder configs
- [skylab_tests] Update skylab tests cros img version
- Fix crash for bogus extensions
- [M111] Disable kPreventNavigationWithoutUserInteraction
- Updating XTBs based on .GRDs from branch 5563
- [M111][Sheriff] Disable flaky customtabs testMultipleActionButtons test
- [M111][Sheriff] Disable flaky customtabs tests
- Merge "Editing: Disable FastPositionIterator feature" to M111 branch
- [M111] Generate conf json for pinpoint only
- Disable glShaderBinary in the passthrough cmd decoder.
- Remove lingered condition for isolation key w.r.t enable-unsafe-webgpu
- Remove BinaryUploadService pointer from RequestHandlerBase
- Merge M111: Revert "AXAPI: expose content from aria-describedby as AXCustomContent"
- [Autofill] Do not store LegalMessageLines at const ref
- [M111] Error if `worker_host_` is not available
- Hide the password leak detection dialog before the account chooser is displayed
- [M111] Don't discard pages that have user edits
- [Merge to M111] Fix IPH parameterized string resolution when ANDROID_SCROLL_OPTIMIZATIONS is disabled
- Revert "5563: Move most/all fuchsia arm64 tests to the temporary LIFO swarming pool"
- Track whether a frame has had user-initiated edits in PerformanceManager
- [Merge-M111][WhatsNew] Fix transition crash from DetailView to TableView
- Roll src/third_party/libwebp/src/ 603e8d7ad..fd7b5d484 (2 commits)
- [M-111] hid: Handle empty input reports
Google Chrome 111.0.5563.64
Security Fixes:
- High CVE-2023-1213: Use after free in Swiftshader. Reported by Jaehun Jeong(@n3sk) of Theori on 2023-01-30
- High CVE-2023-1214: Type Confusion in V8. Reported by Man Yue Mo of GitHub Security Lab on 2023-02-03
- High CVE-2023-1215: Type Confusion in CSS. Reported by Anonymous on 2023-02-17
- High CVE-2023-1216: Use after free in DevTools. Reported by Ganjiang Zhou(@refrain_areu) of ChaMd5-H1 team on 2023-02-21
- High CVE-2023-1217: Stack buffer overflow in Crash reporting. Reported by sunburst of Ant Group Tianqiong Security Lab on 2023-02-03
- High CVE-2023-1218: Use after free in WebRTC. Reported by Anonymous on 2023-02-07
- TBD1415328 High CVE-2023-1219: Heap buffer overflow in Metrics. Reported by Sergei Glazunov of Google Project Zero on 2023-02-13
- TBD1417185 High CVE-2023-1220: Heap buffer overflow in UMA. Reported by Sergei Glazunov of Google Project Zero on 2023-02-17
- Medium CVE-2023-1221: Insufficient policy enforcement in Extensions API. Reported by Ahmed ElMasry on 2022-11-16
- Medium CVE-2023-1222: Heap buffer overflow in Web Audio API. Reported by Cassidy Kim(@cassidy6564) on 2022-12-24
- Medium CVE-2023-1223: Insufficient policy enforcement in Autofill. Reported by Ahmed ElMasry on 2022-12-07
- Medium CVE-2023-1224: Insufficient policy enforcement in Web Payments API. Reported by Thomas Orlita on 2022-12-25
- Medium CVE-2023-1225: Insufficient policy enforcement in Navigation. Reported by Roberto Ffrench-Davis @Lihaft on 2023-01-20
- Medium CVE-2023-1226: Insufficient policy enforcement in Web Payments API. Reported by Anonymous on 2019-10-10
- Medium CVE-2023-1227: Use after free in Core. Reported by @ginggilBesel on 2022-07-31
- Medium CVE-2023-1228: Insufficient policy enforcement in Intents. Reported by Axel Chong on 2022-09-18
- Medium CVE-2023-1229: Inappropriate implementation in Permission prompts. Reported by Thomas Orlita on 2020-12-20
- Medium CVE-2023-1230: Inappropriate implementation in WebApp Installs. Reported by Axel Chong on 2022-12-30
- TBD1274887 Medium CVE-2023-1231: Inappropriate implementation in Autofill. Reported by Yan Zhu, Brave on 2021-11-30
- Low CVE-2023-1232: Insufficient policy enforcement in Resource Timing. Reported by Sohom Datta on 2022-07-24
- Low CVE-2023-1233: Insufficient policy enforcement in Resource Timing. Reported by Soroush Karami on 2020-01-25
- Low CVE-2023-1234: Inappropriate implementation in Intents. Reported by Axel Chong on 2023-01-03
- Low CVE-2023-1235: Type Confusion in DevTools. Reported by raven at KunLun lab on 2023-01-03
- TBD1374518 Low CVE-2023-1236: Inappropriate implementation in Internals. Reported by Alesandro Ortiz on 2022-10-14
Various fixes from internal audits, fuzzing and other initiatives:
- [M111] Disable MediaFoundationD3D11VideoCapture by default
- [M111] media/gpu: Add min output frame pool size for ImageProcessor
- [M111] Restore WebGL contexts on backgrounded pages.
- [M111] Use optional SafeRef to save RenderFrameHost in NavigationRequest
- Updating XTBs based on .GRDs from branch 5563
- [M111] DragDownloadItem: Fix crash by initializing draggingFrame
- Reset the column spanner path when laying out the spanner.
- Reland "Prevent parallel topics in AmbientPhotoController."
- [Merge to M111] CloseAll: Prevent closing a window without a widget
- In Typed CSSOM, reject adding to something that is not a list.
- Updating XTBs based on .GRDs from branch 5563
- [M111] Use "free_space:high" for "Android x64 Builder All Targets (dbg)"
- [M111 Merge] Quick Answers: check context menu before request
- Unify Eviction Surface Collection
Google Chrome 110.0.5481.177
Security Fixes:
- Critical CVE-2023-0941: Use after free in Prompts
- High CVE-2023-0927: Use after free in Web Payments API
- High CVE-2023-0928: Use after free in SwiftShader
- High CVE-2023-0929: Use after free in Vulkan
- High CVE-2023-0930: Heap buffer overflow in Video
- High CVE-2023-0931: Use after free in Video
- TBD1413005 High CVE-2023-0932: Use after free in WebRTC
- Medium CVE-2023-0933: Integer overflow in PDF
Various fixes from internal audits, fuzzing and other initiatives:
- [search_engines] Exclude Policy and Play API engines from Sync merging
- Skip finalizing permission requests in pending queue
- Updating XTBs based on .GRDs from branch 5481
- [v8][wasm] Avoid repeated streaming abortion
- [Merge 100] [privacy sandbox] Fix site-list-entry in lazy loaded list
- [bfcache] NotRestoredReasons return null for non-history/successful bfcache navigation
Google Chrome 110.0.5481.100
- Change log not available for this version
Google Chrome 110.0.5481.96
- Change log not available for this version
Google Chrome 110.0.5481.77
Security Fixes:
- High CVE-2023-0696: Type Confusion in V8
- High CVE-2023-0697: Inappropriate implementation in Full screen mode
- High CVE-2023-0698: Out of bounds read in WebRTC
- Medium CVE-2023-0699: Use after free in GPU
- Medium CVE-2023-0700: Inappropriate implementation in Download
- Medium CVE-2023-0701: Heap buffer overflow in WebUI
- Medium CVE-2023-0702: Type Confusion in Data Transfer
- Medium CVE-2023-0703: Type Confusion in DevTools
- Low CVE-2023-0704: Insufficient policy enforcement in DevTools
- Low CVE-2023-0705: Integer overflow in Core
Various fixes from internal audits, fuzzing and other initiatives:
- Revert "[editing] adjust selection to avoid select `user-select:none` element when triple-click"
- Fix “Change Password on Website” crash
- Updating XTBs based on .GRDs from branch 5481
- [Merge to M110] Add timing histograms to estimate the impact of ClosedTabCache
- [DefaultOffline]: New fonts and remove border radius
- Remove lingered condition for isolation key w.r.t enable-unsafe-webgpu.
- [Merge to M110] Prerender: Record events on PrerenderPageLoadMetricsObserver in UMA
- [CrOS Network] Fix flaky tether dialog test
- [M110] breadcrumbs: fix previous session event overrun
- [M110] Show partial view even when download events are observed by extensions
Google Chrome 109.0.5414.119
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 109.0.5414.87
Security Fixes and Rewards:
- High CVE-2023-0128: Use after free in Overview Mode
- High CVE-2023-0129: Heap buffer overflow in Network Service
- Medium CVE-2023-0130: Inappropriate implementation in Fullscreen API
- Medium CVE-2023-0131: Inappropriate implementation in iframe Sandbox
- Medium CVE-2023-0132: Inappropriate implementation in Permission prompts
- Medium CVE-2023-0133: Inappropriate implementation in Permission prompts
- Medium CVE-2023-0134: Use after free in Cart
- Medium CVE-2023-0135: Use after free in Cart
- Medium CVE-2023-0136: Inappropriate implementation in Fullscreen API
- Medium CVE-2023-0137: Heap buffer overflow in Platform Apps
- Low CVE-2023-0138: Heap buffer overflow in libphonenumber
- Low CVE-2023-0139: Insufficient validation of untrusted input in Downloads
- Low CVE-2023-0140: Inappropriate implementation in File System API
- Low CVE-2023-0141: Insufficient policy enforcement in CORS
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 108.0.5339.124
Security fixes:
- High CVE-2022-4436: Use after free in Blink Media
- High CVE-2022-4437: Use after free in Mojo IPC
- High CVE-2022-4438: Use after free in Blink Frames
- High CVE-2022-4439: Use after free in Aura
- Medium CVE-2022-4440: Use after free in Profiles
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1400487] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 108.0.5339.98
- Change log not available for this version
Google Chrome 108.0.5339.94
Security fixes:
- Type Confusion in V8
Google Chrome 108.0.5339.71
Security Fixes:
- High CVE-2022-4174: Type Confusion in V8
- High CVE-2022-4175: Use after free in Camera Capture
- High CVE-2022-4176: Out of bounds write in Lacros Graphics
- High CVE-2022-4177: Use after free in Extensions
- High CVE-2022-4178: Use after free in Mojo
- High CVE-2022-4179: Use after free in Audio
- High CVE-2022-4180: Use after free in Mojo
- High CVE-2022-4181: Use after free in Forms
- Medium CVE-2022-4182: Inappropriate implementation in Fenced Frames
- Medium CVE-2022-4183: Insufficient policy enforcement in Popup Blocker
- Medium CVE-2022-4184: Insufficient policy enforcement in Autofill
- Medium CVE-2022-4185: Inappropriate implementation in Navigation
- Medium CVE-2022-4186: Insufficient validation of untrusted input in Downloads
- Medium CVE-2022-4187: Insufficient policy enforcement in DevTools
- Medium CVE-2022-4188: Insufficient validation of untrusted input in CORS
- Medium CVE-2022-4189: Insufficient policy enforcement in DevTools
- Medium CVE-2022-4190: Insufficient data validation in Directory
- Medium CVE-2022-4191: Use after free in Sign-In
- Medium CVE-2022-4192: Use after free in Live Caption
- Medium CVE-2022-4193: Insufficient policy enforcement in File System API
- Medium CVE-2022-4194: Use after free in Accessibility
- Medium CVE-2022-4195: Insufficient policy enforcement in Safe Browsing
As usual, our ongoing internal security work was responsible for a wide range of fixes
- [1394280] Various fixes from internal audits, fuzzing and other initiative
Google Chrome 107.0.5304.121
Security fixes:
- High CVE-2022-4135: Heap buffer overflow in GPU
Google Chrome 107.0.5304.110
Security Fixes and Rewards:
- High CVE-2022-3885: Use after free in V8
- High CVE-2022-3886: Use after free in Speech Recognition
- High CVE-2022-3887: Use after free in Web Workers
- High CVE-2022-3888: Use after free in WebCodecs
- High CVE-2022-3889: Type Confusion in V8
- High CVE-2022-3890: Heap buffer overflow in Crashpad
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1382280] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 107.0.5304.87
Security Fixes:
- High CVE-2022-3723: Type Confusion in V8
Google Chrome 107.0.5304.62
Security Fixes:
- High CVE-2022-3652: Type Confusion in V8
- High CVE-2022-3653: Heap buffer overflow in Vulkan
- High CVE-2022-3654: Use after free in Layout
- Medium CVE-2022-3655: Heap buffer overflow in Media Galleries
- Medium CVE-2022-3656: Insufficient data validation in File System
- Medium CVE-2022-3657: Use after free in Extensions
- Medium CVE-2022-3658: Use after free in Feedback service on Chrome OS
- Medium CVE-2022-3659: Use after free in Accessibility
- Medium CVE-2022-3660: Inappropriate implementation in Full screen mode
- Low CVE-2022-3661: Insufficient data validation in Extensions
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1377543] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 106.0.5249.119
This update includes 6 security fixes:
- High CVE-2022-3445: Use after free in Skia
- High CVE-2022-3446: Heap buffer overflow in WebSQL
- High CVE-2022-3447: Inappropriate implementation in Custom Tabs
- High CVE-2022-3448: Use after free in Permissions API
- High CVE-2022-3449: Use after free in Safe Browsing
- High CVE-2022-3450: Use after free in Peer Connection
Other fixes:
- Updating XTBs based on .GRDs from branch 5249
- [Merge to M106] Use HeapMojoReceiver rather than mojo::Receiver for PeerConnectionTracker
- [skylab_tests] Update skylab tests cros img version
- [M106] Reset the profile pointer in PreferenceValidationDelegate before the profile is destroyed.
- 7e1399e [GURL] Migrate referrer to use GURL
- [M106] infra: Fetch //chrome/VERSION onto orchestrator builds
- Show about:blank in CCTs
- [M106] Reland "remove .vpython"
- chromeos: Disable failing u2fd.WebauthnUsingPassword.*
- [M106] Avoid showing toast after BrandingController destroyed
- [SearchResumption] Add user actions and histogram
- Fix UAF issue around permission status observer list
- CaptivePortalDetector: Test |detection_callback_|
- [M106] sqlite: Upgrade to 3.39.4
- AT actions API: Always expose default action at index 0
- [M106] Clipboard paste: use browser-safe version of user activation
- [CacheStorage] GetStorageKeys shouldn't rely on QuotaManagerProxy
- [M106 merge] Make password fields spellcheck-disabled by default
- [M106] Remove SERVICE_ACCOUNT_JSON from logdog wrapper
- Add missing early return in RunLegacyDataUseMeasurment experiment
- Updating XTBs based on .GRDs from branch 5249
Google Chrome 106.0.5249.103
- Change log not available for this version
Google Chrome 106.0.5249.91
- Change log not available for this version
Google Chrome 106.0.5249.61
Security Fixes:
- High CVE-2022-3304: Use after free in CSS
- High CVE-2022-3201: Insufficient validation of untrusted input in Developer Tools
- High CVE-2022-3305: Use after free in Survey
- High CVE-2022-3306: Use after free in Survey
- High CVE-2022-3307: Use after free in Media
- Medium CVE-2022-3308: Insufficient policy enforcement in Developer Tools
- Medium CVE-2022-3309: Use after free in Assistant
- Medium CVE-2022-3310: Insufficient policy enforcement in Custom Tabs
- Medium CVE-2022-3311: Use after free in Import
- Medium CVE-2022-3312: Insufficient validation of untrusted input in VPN
- Medium CVE-2022-3313: Incorrect security UI in Full Screen
- Medium CVE-2022-3314: Use after free in Logging
- Medium CVE-2022-3315: Type confusion in Blink
- Low CVE-2022-3316: Insufficient validation of untrusted input in Safe Browsing
- Low CVE-2022-3317: Insufficient validation of untrusted input in Intents
- Low CVE-2022-3318: Use after free in ChromeOS Notifications
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1368115] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 105.0.5195.127
Security Fixes and Rewards:
- High CVE-2022-3195: Out of bounds write in Storage
- High CVE-2022-3196: Use after free in PDF
- High CVE-2022-3197: Use after free in PDF
- High CVE-2022-3198: Use after free in PDF
- High CVE-2022-3199: Use after free in Frames
- High CVE-2022-3200: Heap buffer overflow in Internals
- High CVE-2022-3201: Insufficient validation of untrusted input in DevTools
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1363148] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 105.0.5195.102
Security fixes:
- High CVE-2022-3075: Insufficient data validation in Mojo
Google Chrome 105.0.5195.54
Security Fixes:
- Critical CVE-2022-3038: Use after free in Network Service
- High CVE-2022-3039: Use after free in WebSQL
- High CVE-2022-3040: Use after free in Layout
- High CVE-2022-3041: Use after free in WebSQL
- High CVE-2022-3042: Use after free in PhoneHub
- High CVE-2022-3043: Heap buffer overflow in Screen Capture
- High CVE-2022-3044: Inappropriate implementation in Site Isolation
- High CVE-2022-3045: Insufficient validation of untrusted input in V8
- High CVE-2022-3046: Use after free in Browser Tag
- Medium CVE-2022-3047: Insufficient policy enforcement in Extensions API
- Medium CVE-2022-3048: Inappropriate implementation in Chrome OS lockscreen
- Medium CVE-2022-3049: Use after free in SplitScreen
- Medium CVE-2022-3050: Heap buffer overflow in WebUI
- Medium CVE-2022-3051: Heap buffer overflow in Exosphere
- Medium CVE-2022-3052: Heap buffer overflow in Window Manager
- Medium CVE-2022-3053: Inappropriate implementation in Pointer Lock
- Medium CVE-2022-3054: Insufficient policy enforcement in DevTools
- Medium CVE-2022-3055: Use after free in Passwords
- Low CVE-2022-3056: Insufficient policy enforcement in Content Security Policy
- Low CVE-2022-3057: Inappropriate implementation in iframe Sandbox
- Low CVE-2022-3058: Use after free in Sign-In Flow
Various fixes from internal audits, fuzzing and other initiatives:
- Create separate copies of PasswordForms instead of keeping raw pointers
- Use CancelableCallback in ForcedProfileSwitchInterceptionHandle to avoid use-after-free
- Updating XTBs based on .GRDs from branch 5195
- bindings: Remove the prototype chain from observable array handler object
- Revert "[Merge-105][Dr-Dc] Add more devices to be blocklisted."
- Revert "[Merge-105][Dr-Dc] Disable DrDc on some gpus ."
- [M105 Merge][fieldtrial] Add config for NotifyJavaSpuriouslyToMeasurePerf
- [M105] Change API used to show the Tailored Security Desktop Dialog
- [M105 Merge][WebContentsObserverProxy] Add metric for didStartNavigation
- [Merge to M105] Fix buffer overflow in ax_platform_node_auralinux
- Merge 105 / Address flaky test: MultipleBadAccessibilityIPCsKillsRenderer
- [Merge 105] Revert "Add alternate accelerator for IDC_BASIC_PRINT and deprecate the old one"
- [M105 Merge][WebContentsImpl] Don't call DidStartNavigation in child frames
- Handle null WebContents when checking display ID
- [lacros] Update lacros QA qualified version
- [Merge-105][Dr-Dc] Add more devices to be blocklisted
- [CPA] Added feature engagement rate limits to action chip
- [m105][rollicu] Update TZ to 2022b
- [Merge-105][Dr-Dc] Disable DrDc on some gpus
- [M105][infra] Use 8-core machines for branched try/fuchsia-binary-size
- [M105 Merge][SequenceManagerImpl] Increase temp queue capacity to avoid extra alloc
- [M105 Merge][fieldtrial] Add config for jank experiments
- [Start] Fix Start surface doesn't response when changing homepage settings
- [SearchResumption] Change search resumption module header text
- Updating XTBs based on .GRDs from branch 5195
- [Merge to M105] ServiceWorker: Don't run update check during browser shutdown
Google Chrome 104.0.5112.101
Security fixes:
- Critical CVE-2022-2852: Use after free in FedCM
- High CVE-2022-2854: Use after free in SwiftShader
- High CVE-2022-2855: Use after free in ANGLE
- High CVE-2022-2857: Use after free in Blink
- High CVE-2022-2858: Use after free in Sign-In Flow
- High CVE-2022-2853: Heap buffer overflow in Downloads
- High CVE-2022-2856: Insufficient validation of untrusted input in Intents
- Medium CVE-2022-2859: Use after free in Chrome OS Shell
- Medium CVE-2022-2860: Insufficient policy enforcement in Cookies
- Medium CVE-2022-2861: Inappropriate implementation in Extensions API
Google Chrome 103.0.5060.134
Security Fixes:
- High CVE-2022-2477 : Use after free in Guest View
- High CVE-2022-2478 : Use after free in PDF
- High CVE-2022-2479 : Insufficient validation of untrusted input in File
- High CVE-2022-2480 : Use after free in Service Worker API
- High CVE-2022-2481: Use after free in Views
- Low CVE-2022-2163: Use after free in Cast UI and Toolbar
Various fixes from internal audits, fuzzing and other initiatives:
- Keep refptr to ServiceWorkerVersion in MaybeTimeoutRequest
- Updating XTBs based on .GRDs from branch 5060
- Updating XTBs based on .GRDs from branch 5060
- Fix incorrect text itemization for r codepoint
- Updating XTBs based on .GRDs from branch 5060
- [M103 Merge] Fix UAF in CloseBubbleOnTabActivationHelper
- [M103]Fix an issue that content URI can be used to upload files under app dir
- [M103] Allow GPU M1 Macs to use Mac 12
- Fix dawn write handle data update OOB check
- [M103] Reland "Fix UaF in media router dialog"
- Updating XTBs based on .GRDs from branch 5060
- Disable failing test.
- Updating XTBs based on .GRDs from branch 5060
- [OSCrypt] Fix branded GnomeKeyring tests
- [M103][Messages][SaveCard] Fix metrics recording error
- Updating XTBs based on .GRDs from branch 5060
- Try to avoid blocking reads in InputStream reading code
- M103: Use weak ptr for webview JavaScriptDialogHelper callback
- [Sheriff] Restore flaky test expectation for mouse-events-on-node-deletion
- [M103][Messages][SaveCard] Reset metric recording related variables.
- Updating XTBs based on .GRDs from branch 5060
- WebGPU: Mark the context lost on GPU context lost
- Mitigate bad cast in OffscreenCanvas::GetFontSelector
- Filter command responses from detached CDP sessions
- [Merge to 103] Merge fix for crash when enabling calendar in M103"
- Disable flaky InspectUIFencedFrameTest.FencedFrameInFrontEnd
Google Chrome 103.0.5060.114
Security Fixes:
- High CVE-2022-2294: Heap buffer overflow in WebRTC
- High CVE-2022-2295: Type Confusion in V8
- High CVE-2022-2296: Use after free in Chrome OS Shell
Various fixes from internal audits, fuzzing and other initiatives:
- Pre-paint: OOF within monolithic content is contained normally
- Pre-paint: Remove obsolete inline continuation code
- Updating XTBs based on .GRDs from branch 5060
- Switch V8 reference to git hash
- Automatic update from google3
- HDR/Windows: SDR displays must have 80 nits
- Updating XTBs based on .GRDs from branch 5060
- Disable IntegrationTest.SelfUpdateFromOldReal in M103
- Add bot account to transport_security_state_static owners
- M103: [Pinpoint] add pgo bots to M103
- Updating XTBs based on .GRDs from branch 5060
- migrate metrics_python_tests to python3 for M103
- [Sheriff] Disable flaky MachOImageAnnotationsReader tests for M103
- Revert "Move most of partnerbookmarks to the module"
- [M103] Let GPU Intel Macs target 12.4
- Updating XTBs based on .GRDs from branch 5060
- testing: fix check_static_initializers.py for python3 for M103
- sheriff: Disable QuarantineMacTest.*
- [M103] Disable svg/W3C-SVG-1.1/pservers-grad-05-b.svg to satisfy M103 builders
- Updating XTBs based on .GRDs from branch 5060
- Updating XTBs based on .GRDs from branch 5060
- [M103] Disabled crashing test in FirstRunActivitySigninAndSyncTest
- Change ShouldDisableDohForManaged to use IsEnrolledToDomain()
- [Merge 103]Revert "Refresh policies from Registry dynamically"
- 5060: infra: Add the root vpython spec files to orchestrator runtime deps
- [Merge 103] crOS: Support SecondaryGoogleAccountUsage policy
- [Merge103] Fix context nullptr crash
- Updating XTBs based on .GRDs from branch 5060
Google Chrome 103.0.5060.66
- Change log not available for this version
Google Chrome 103.0.5060.53
- Change log not available for this version
Google Chrome 102.0.5005.115
Security Fixes:
- High CVE-2022-2007: Use after free in WebGPU. Reported by David Manouchehri on 2022-05-17
- High CVE-2022-2008: Out of bounds memory access in WebGL. Reported by khangkito - Tran Van Khang (VinCSS) on 2022-04-19
- High CVE-2022-2010: Out of bounds read in compositing. Reported by Mark Brand of Google Project Zero on 2022-05-13
- High CVE-2022-2011: Use after free in ANGLE. Reported by SeongHwan Park (SeHwa) on 2022-05-31
Various fixes from internal audits, fuzzing and other initiatives:
- [Merge 102] Disable the enterprise dialog being showed for all users
- Revert "Post media log destruction to avoid destruction"
- Post media log destruction to avoid destruction
- [M102] Migrate "chromium.memory:Linux TSan Builder" src side
- Ensure the link data checkbox is always on top of the action buttons
- Set selection range after committed composition only for non-IME input
- Updating XTBs based on .GRDs from branch 5005
- [Reland][Region Capture] Fix blocking of other-tab captures
- [M102] Revert "Remove the AcceptCHFrame base::Feature"
- PaintOpReader: Harden PaintImage deserialization
- [102] Revert "Enable same-process, cross-origin iframe throttle by default."
- [M102][Color Pipeline] Fix extensions badge contrast
- Use the right tex target for video frame for ANGLE/Metal
- Merge M102: "Retrieve optional video profiles asynchronously."
- [Merge 102] [journeys] Respect AllowDeletingBrowserHistory in WebUI Handler
- [M102] Fix a regression that CascadeLayerMap is not rebuilt
- CHECK that detaching a mapped GPUBuffer was successful
- [Merge to M102] [RPM] Add check for 2021 signing key
Google Chrome 102.0.5005.63
Security Fixes:
- Critical CVE-2022-1853: Use after free in Indexed DB
- High CVE-2022-1854: Use after free in ANGLE
- High CVE-2022-1855: Use after free in Messaging
- High CVE-2022-1856: Use after free in User Education
- High CVE-2022-1857: Insufficient policy enforcement in File System API
- High CVE-2022-1858: Out of bounds read in DevTools
- High CVE-2022-1859: Use after free in Performance Manager
- High CVE-2022-1860: Use after free in UI Foundations
- High CVE-2022-1861: Use after free in Sharing
- Medium CVE-2022-1862: Inappropriate implementation in Extensions
- Medium CVE-2022-1863: Use after free in Tab Groups
- Medium CVE-2022-1864: Use after free in WebApp Installs
- Medium CVE-2022-1865: Use after free in Bookmarks
- Medium CVE-2022-1866: Use after free in Tablet Mode
- Medium CVE-2022-1867: Insufficient validation of untrusted input in Data Transfer
- Medium CVE-2022-1868: Inappropriate implementation in Extensions API
- Medium CVE-2022-1869: Type Confusion in V8
- Medium CVE-2022-1870: Use after free in App Service
- Low CVE-2022-1871: Insufficient policy enforcement in File System API
- Low CVE-2022-1872: Insufficient policy enforcement in Extensions API
- Low CVE-2022-1873: Insufficient policy enforcement in COOP
- Low CVE-2022-1874: Insufficient policy enforcement in Safe Browsing
- Low CVE-2022-1875: Inappropriate implementation in PDF
- Low CVE-2022-1876: Heap buffer overflow in DevTools
As usual, our ongoing internal security work was responsible for a wide range of fixes:
- [1328866] Various fixes from internal audits, fuzzing and other initiatives
Google Chrome 101.0.4951.64
Security fixes:
- High CVE-2022-1633: Use after free in Sharesheet
- High CVE-2022-1634: Use after free in Browser UI
- High CVE-2022-1635: Use after free in Permission Prompts
- High CVE-2022-1636: Use after free in Performance APIs
- High CVE-2022-1637: Inappropriate implementation in Web Contents
- High CVE-2022-1638: Heap buffer overflow in V8 Internationalization
- High CVE-2022-1639: Use after free in ANGLE
- High CVE-2022-1640: Use after free in Sharing
- Medium CVE-2022-1641: Use after free in Web UI Diagnostics
Google Chrome 101.0.4951.54
- Change log not available for this version
Google Chrome 101.0.4951.41
Security Fixes:
- High CVE-2022-1477: Use after free in Vulkan
- High CVE-2022-1478: Use after free in SwiftShader
- High CVE-2022-1479: Use after free in ANGLE
- High CVE-2022-1480: Use after free in Device API
- High CVE-2022-1481: Use after free in Sharing
- High CVE-2022-1482: Ippropriate implementation in WebGL
- High CVE-2022-1483: Heap buffer overflow in WebGPU
- Medium CVE-2022-1484: Heap buffer overflow in Web UI Settings
- Medium CVE-2022-1485: Use after free in File System API
- Medium CVE-2022-1486: Type Confusion in V8
- Medium CVE-2022-1487: Use after free in Ozone
- Medium CVE-2022-1488: Ippropriate implementation in Extensions API
- Medium CVE-2022-1489: Out of bounds memory access in UI Shelf
- Medium CVE-2022-1490: Use after free in Browser Switcher
- Medium CVE-2022-1491: Use after free in Bookmarks
- Medium CVE-2022-1492: Insufficient data validation in Blink Editing
- Medium CVE-2022-1493: Use after free in Dev Tools
- Medium CVE-2022-1494: Insufficient data validation in Trusted Types
- Medium CVE-2022-1495: Incorrect security UI in Downloads
- Medium CVE-2022-1496: Use after free in File Mager
- Medium CVE-2022-1497: Ippropriate implementation in Input
- Low CVE-2022-1498: Ippropriate implementation in HTML Parser
- Low CVE-2022-1499: Ippropriate implementation in WebAuthentication
- TBD1223475 Low CVE-2022-1500: Insufficient data validation in Dev Tools
- Low CVE-2022-1501: Ippropriate implementation in iframe
Various fixes from internal audits, fuzzing and other initiative:
- Speculative fix for crashes in ScrollableArea::InjectGestureScrollEvent
- Check for error when calling ComputeImageSizeInBytes
- [M101] Ensure that thin testers do not set reclient properties
- sheriff: Disable DiagnosticsAppWithInput.BrowserTest on ChromeOS
- [Sheriff] Disable PolicyToPrefsMapping or ChromeOS dbg
- [M101] Allow for setting try_settings without mirrors
- ServiceImageTransferCacheEntry: Fix uninitialized values
- Check Membership requests should only occur on fresh local state prefs
- [M101][QrCode] Fix QR code icon not appearing in the omnibox for CrOS
- Temporarily disable opening file:// on Android TM
- [M101][infra] Create test specs for linux-blink-rel-dummy try builders
- Don't consume user activation when opening windows in WebView
- Aw: Add the missing ALGORITHMIC_DARKENING
- [M101] stts: don't hold raw view->controller pointer
- SessionRestore: Ensure locked profile sessions are not restored
- Updating XTBs based on .GRDs from branch 4951
- Switch to use WaitForLoadStop to fix flakiness
- Move downloaded models to a randomly generated directory
- M101: Prevent the creation of a duplicate dialog in CupsPrintersHandler
- M101: Prevent the creation of a duplicate dialog in ScanningHandler
- libwebp: update to 1.2.2 (20ef03e)
- m101: Fix dangling pointer in DevToolsUIBindingsEnabler
- [PriceTracking] Add a flag for whether to parse seen offer to server
- [M101][infra] Migrate builder config for chromeos-kevin-rel src-side
- [Merge M101]: Fix crash when stopping speech recognition before it has initialized
- Revert "CCA: Avoid CameraHalDelegate Leak from VCDF"
- Revert "CCA: Moves a Thread subordinate to CameraHalDelegate to its variable"
- Fix null pointer exception in PersistedTabData
- [Merge M101]: SpeechRecognitionPrivate: Prevent dangling callbacks
- Privacy Sandbox Settings: Fix V2 settings always show as on
- Add bounds check to WebGPUDecoderImpl::DoRequestDevice
- [M101] Sanitize DragData markup before inserting it into document
Google Chrome 100.0.4896.127
- Change log not available for this version
Google Chrome 100.0.4896.88
- [Fuchsia] Handle encryption config change in WebEngineAudioRenderer
- Revert "[M100 Merge] Add a crash key "list-of-hung-threads" in the GPU watchdog"
- Crostini_upgrader: Handle content::WebContents through weak pointers
- Disable extension content script IPC enforcement
- [M100][infra] Migrate configs for Android x64 Builder (dbg) src-side
- M100: syncfs_internals: Use WeakPtr for DumpDatabaseHandler
- MediaDevices: Prevent iterator invalidation during Promise resolution
- Fix letterSpacing/wordSpacing for Canvas.Style
- Partial revert of "Updater: Fix signing."
- Updating XTBs based on .GRDs from branch 4896
- Switch to use WaitForLoadStop to fix flakiness
- [Merge 100][iOS] Fix new new FRE bug
- [M100][infra] Migrate configs for Android arm Builder (dbg) src-side
- DGAPI: Flip runtime feature back to "experimental" (merge to M100)
- R[Merge M100] Put Android font lookup cache behind a featureevert "Fix an edge case bug in Windows TSF1 implementation."
- [Merge M100] Put Android font lookup cache behind a feature[M100] Remove noop scheduler job for Win11 Tests x64.
- [M100] Remove noop scheduler job for Win11 Tests x64.
- [M100 Merge] Add a crash key "list-of-hung-threads" in the GPU watchdog
- [m100 cherrypick] Disable IME at non password fields when not at the normal screen
- [Merge to M100] Reland "Expect non-initial NavigationEntry with empty URL on session restore"
- Revert "Enable to iterate DedicatedWorkers from their creators: LocalDOMWindow or DedicatedWorkerGlobalScope"
- Fix crash with JAWS screen reader
- FrameSinkBundle: Lazily observe BeginFrameSource
- Extend force-color-profile forever
- [css-typed-om] Disallow CSS-wide keywords for StylePropertyMap.set
- M100: Change ownership of BlobBytesProvider
- Updating XTBs based on .GRDs from branch 4896
- [M100][infra] Migrate configs for Win x64 Builder src-side
- [skia_renderer]: Use RectF::Intersect in ApplyScissor
- Turn off the Digital Goods API on Android for now, to work around a crash on WebView
- Custom themes should override native color definitions
Security fixes:
- High CVE-2022-1305: Use after free in storage
- High CVE-2022-1306: Inappropriate implementation in compositing
- High CVE-2022-1307: Inappropriate implementation in full screen
- High CVE-2022-1308: Use after free in BFCache
- High CVE-2022-1309: Insufficient policy enforcement in developer tools
- High CVE-2022-1310: Use after free in regular expressions
- High CVE-2022-1311: Use after free in Chrome OS shell
- High CVE-2022-1312: Use after free in storage
- Medium CVE-2022-1313: Use after free in tab groups
- Medium CVE-2022-1314: Type Confusion in V8
Google Chrome 100.0.4896.75
- Updating XTBs based on .GRDs from branch 4896
- Rework menu_bg_tinted to not span deps.
- Revert "Reland "[Tab Switcher] Refactor - moved aspect ratio determination to helper method. Added static aspect ratio for tablet. Added a couple unit tests for new method in TabUtils""
- [m100 cherrypick] Disable autocorrect for system PK at lock screen
- [M100 merge] history: don't handle db error during destruction
- Avoid spawning HangWatcher thread in the GPU process due to conflict with WatchDog
- Allow sdpSemantics:'plan-b' from the web always on Fuchsia
- Updating XTBs based on .GRDs from branch 4896
- [LaCrOS]Temporary workaround to disable RED_8 overlay candidates&l
 OperaOpera 109.0 Build 5097.68
OperaOpera 109.0 Build 5097.68 PhotoshopAdobe Photoshop CC 2024 25.7
PhotoshopAdobe Photoshop CC 2024 25.7 PrivadoVPNPrivadoVPN 3.8.11
PrivadoVPNPrivadoVPN 3.8.11 ReiBootTenorshare ReiBoot iOS for Mac 9.4.4
ReiBootTenorshare ReiBoot iOS for Mac 9.4.4 Adobe AcrobatAdobe Acrobat Pro 2024.002.20736
Adobe AcrobatAdobe Acrobat Pro 2024.002.20736 OKXOKX - Buy Bitcoin or Ethereum
OKXOKX - Buy Bitcoin or Ethereum ParallelsParallels Desktop 19.3.1
ParallelsParallels Desktop 19.3.1 TradingViewTradingView - Track All Markets
TradingViewTradingView - Track All Markets CleanMyMacCleanMyMac X 4.15.3
CleanMyMacCleanMyMac X 4.15.3 4DDiG4DDiG Mac Data Recovery 3.4.2
4DDiG4DDiG Mac Data Recovery 3.4.2








Comments and User Reviews