-
Latest Version
-
Operating System
Mac OS X
-
User Rating
Click to vote -
Author / Product
-
Filename
jdk-21_macos-x64_bin.dmg
-
MD5 Checksum
b4486cb1ba6af82b5230eab04cc2df41
Sometimes latest versions of the software can cause issues when installed on older devices or devices running an older version of the operating system.
Software makers usually fix these issues but it can take them some time. What you can do in the meantime is to download and install an older version of Java JDK 21.
For those interested in downloading the most recent release of Java Development Kit for Mac or reading our review, simply click here.
All old versions distributed on our website are completely virus-free and available for download at no cost.
We would love to hear from you
If you have any questions or ideas that you want to share with us - head over to our Contact page and let us know. We value your feedback!
 OperaOpera 119.0 Build 5497.141
OperaOpera 119.0 Build 5497.141 PhotoshopAdobe Photoshop CC 2024 25.12
PhotoshopAdobe Photoshop CC 2024 25.12 CapCutCapCut 6.5.0
CapCutCapCut 6.5.0 BlueStacksBlueStacks Air 5.21.650
BlueStacksBlueStacks Air 5.21.650 Adobe AcrobatAdobe Acrobat Pro 2025.001.20529
Adobe AcrobatAdobe Acrobat Pro 2025.001.20529 MacKeeperMacKeeper 7.0
MacKeeperMacKeeper 7.0 Hero WarsHero Wars - Online Action Game
Hero WarsHero Wars - Online Action Game SemrushSemrush - Keyword Research Tool
SemrushSemrush - Keyword Research Tool CleanMyMacCleanMyMac X 5.0.6
CleanMyMacCleanMyMac X 5.0.6 4DDiG4DDiG Mac Data Recovery 5.2.2
4DDiG4DDiG Mac Data Recovery 5.2.2
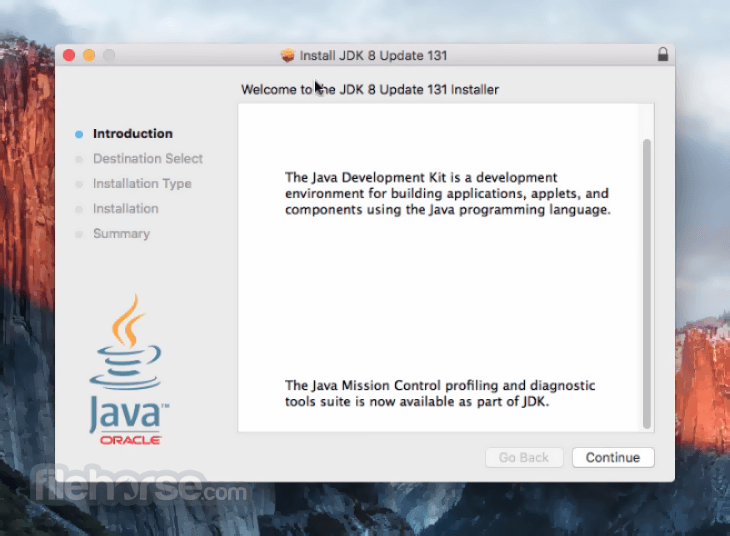
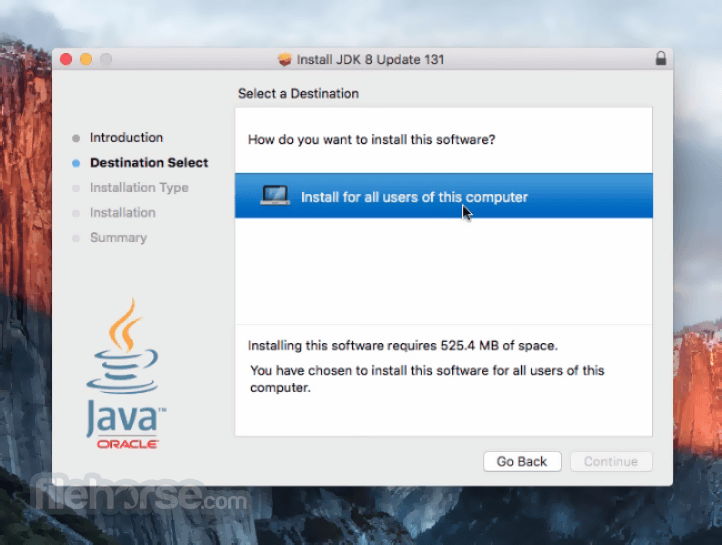
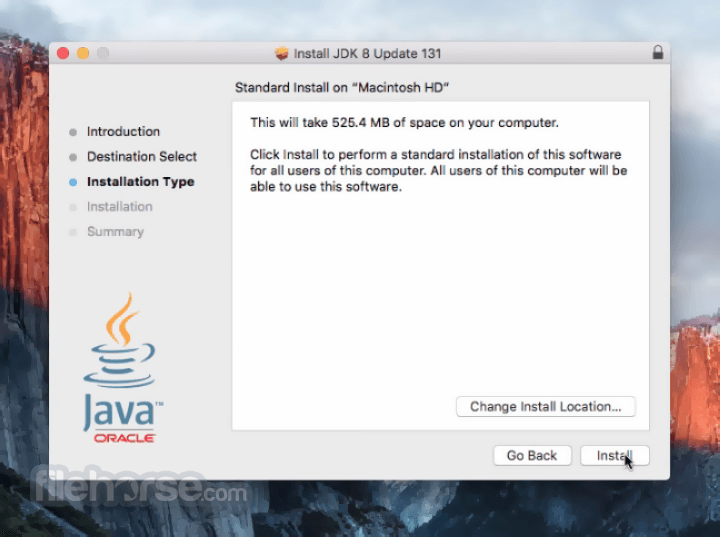
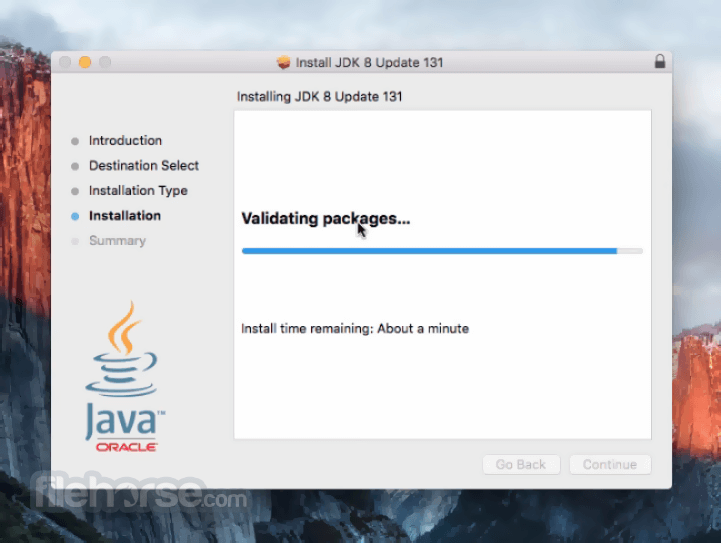





Comments and User Reviews