-
Latest Version
-
Operating System
Mac OS X
-
User Rating
Click to vote -
Author / Product
-
Filename
jre-8u131-macosx-x64.dmg
-
MD5 Checksum
53e92c10747fe102ee5a03bef45c0fb8
Sometimes latest versions of the software can cause issues when installed on older devices or devices running an older version of the operating system. Software makers usually fix these issues but it can take them some time. What you can do in the meantime is to download and install an older version of Java JRE 8 Update 131.
For those interested in downloading the most recent release of Java Runtime Environment for Mac or reading our review, simply click here.
All old versions distributed on our website are completely virus-free and available for download at no cost.
We would love to hear from you
If you have any questions or ideas that you want to share with us - head over to our Contact page and let us know. We value your feedback!
-
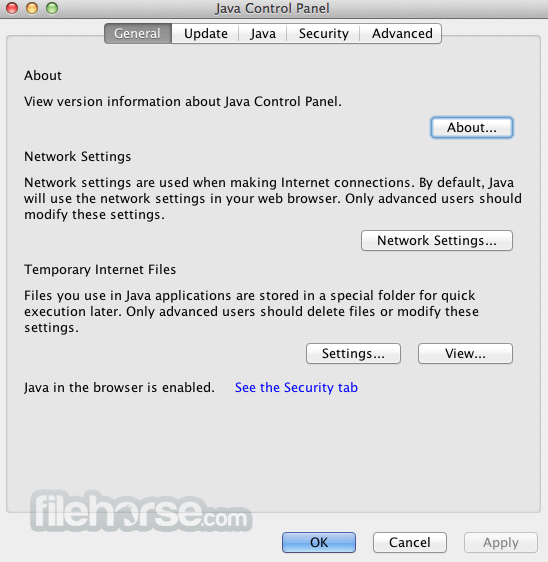
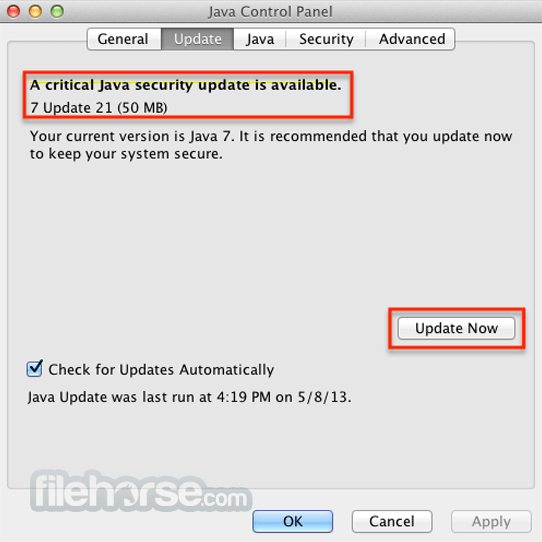
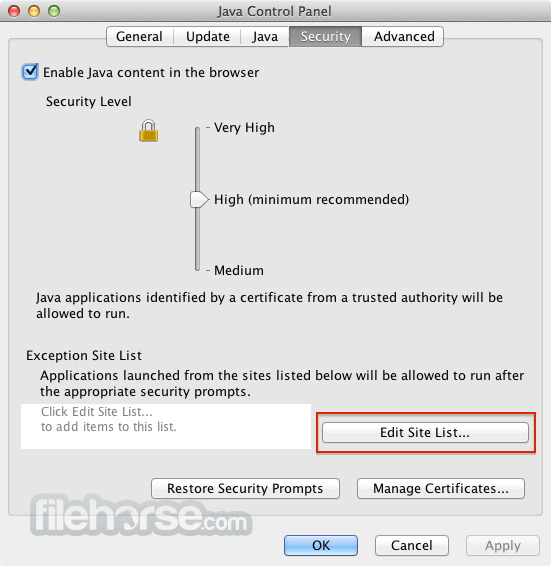
Java JRE 8 Update 131 Screenshots
The images below have been resized. Click on them to view the screenshots in full size.
What's new in this version:
CHANGES:
MD5 added to jdk.jar.disabledAlgorithms Security property:
This JDK release introduces a new restriction on how MD5 signed JAR files are verified. If the signed JAR file uses MD5, signature verification operations will ignore the signature and treat the JAR as if it were unsigned. This can potentially occur in the following types of applications that use signed JAR files:
- Applets or Web Start Applications
- Standalone or Server Applications that are run with a SecurityManager enabled and are configured with a policy file that grants permissions based on the code signer(s) of the JAR file.
- The list of disabled algorithms is controlled via the security property, jdk.jar.disabledAlgorithms, in the java.security file. This property contains a list of disabled algorithms and key sizes for cryptographically signed JAR files.
- To check if a weak algorithm or key was used to sign a JAR file, one can use the jarsigner binary that ships with this JDK. Running "jarsigner -verify" on a JAR file signed with a weak algorithm or key will print more information about the disabled algorithm or key.
New system property to control caching for HTTP SPNEGO connection:
- A new JDK implementation specific system property to control caching for HTTP SPNEGO (Negotiate/Kerberos) connections is introduced. Caching for HTTP SPNEGO connections remains enabled by default, so if the property is not explicitly specified, there will be no behavior change.
- When connecting to an HTTP server that uses SPNEGO to negotiate authentication, and when connection and authentication with the server is successful, the authentication information will then be cached and reused for further connections to the same server. In addition, connecting to an HTTP server using SPNEGO usually involves keeping the underlying connection alive and reusing it for further requests to the same server. In some applications, it may be desirable to disable all caching for the HTTP SPNEGO (Negotiate/Kerberos) protocol in order to force requesting new authentication with each new request to the server.
With this change, we now provide a new system property that allows control of the caching policy for HTTP SPNEGO connections. If jdk.spnego.cache is defined and evaluates to false, then all caching will be disabled for HTTP SPNEGO connections. Setting this system property to false may, however, result in undesirable side effects:
- Performance of HTTP SPNEGO connections may be severely impacted as the connection will need to be re-authenticated with each new request, requiring several communication exchanges with the server.
- Credentials will need to be obtained again for each new request, which, depending on whether transparent authentication is available or not, and depending on the global Authenticator implementation, may result in a popup asking the user for credentials for every new request.
New system property to control caching for HTTP NTLM connection:
- A new JDK implementation specific system property to control caching for HTTP NTLM connection is introduced. Caching for HTTP NTLM connection remains enabled by default, so if the property is not explicitly specified, there will be no behavior change.
- On some platforms, the HTTP NTLM implementation in the JDK can support transparent authentication, where the system user credentials are used at system level. When transparent authentication is not available or unsuccessful, the JDK only supports getting credentials from a global authenticator. If connection to the server is successful, the authentication information will then be cached and reused for further connections to the same server. In addition, connecting to an HTTP NTLM server usually involves keeping the underlying connection alive and reusing it for further requests to the same server. In some applications, it may be desirable to disable all caching for the HTTP NTLM protocol in order to force requesting new authentication with each new requests to the server.
With this change, we now provide a new system property that allows control of the caching policy for HTTP NTLM connections. If jdk.ntlm.cache is defined and evaluates to false, then all caching will be disabled for HTTP NTLM connections. Setting this system property to false may, however, result in undesirable side effects:
- Performance of HTTP NTLM connections may be severely impacted as the connection will need to be re-authenticated with each new request, requiring several communication exchanges with the server.
- Credentials will need to be obtained again for each new request, which, depending on whether transparent authentication is available or not, and depending on the global Authenticator implementation, may result in a popup asking the user for credentials for every new request.
New version of VisualVM:
- VisualVM 1.3.9 was released on October 4th, 2016 and has been integrated into 8u131
BUG FIXES:
Correction of IllegalArgumentException from TLS handshake:
- A recent issue from the JDK-8173783 fix can cause issue for some TLS servers. The problem originates from an IllegalArgumentException thrown by the TLS handshaker code: java.lang.IllegalArgumentException: System property jdk.tls.namedGroups(null) contains no supported elliptic curves. The issue can arise when the server doesn't have elliptic curve cryptography support to handle an elliptic curve name extension field (if present). Users are advised to upgrade to this release. By default, JDK 7 Updates and later JDK families ship with the SunEC security provider which provides elliptic curve cryptography support. Those releases should not be impacted unless security providers are modified
 OperaOpera 109.0 Build 5097.45
OperaOpera 109.0 Build 5097.45 PhotoshopAdobe Photoshop CC 2024 25.6
PhotoshopAdobe Photoshop CC 2024 25.6 PrivadoVPNPrivadoVPN 3.8.11
PrivadoVPNPrivadoVPN 3.8.11 ReiBootTenorshare ReiBoot iOS for Mac 9.4.4
ReiBootTenorshare ReiBoot iOS for Mac 9.4.4 Adobe AcrobatAdobe Acrobat Pro 2024.002.20687
Adobe AcrobatAdobe Acrobat Pro 2024.002.20687 OKXOKX - Buy Bitcoin or Ethereum
OKXOKX - Buy Bitcoin or Ethereum ParallelsParallels Desktop 19.3.0
ParallelsParallels Desktop 19.3.0 TradingViewTradingView - Track All Markets
TradingViewTradingView - Track All Markets CleanMyMacCleanMyMac X 4.15.3
CleanMyMacCleanMyMac X 4.15.3 4DDiG4DDiG Mac Data Recovery 3.4.2
4DDiG4DDiG Mac Data Recovery 3.4.2




Comments and User Reviews